
Caller ID spoofing has become a real nuisance with machines and scammers hiding behind a number that they are not authorized to use. This creates the need to prevent illegitimate calls from using random numbers. In the meantime, have you ever wondered how easy it is to spoof a caller ID?
What software is needed?
There are many online services that allow people to spoof calls, but it is possible for someone to spoof caller IDs without these services. To spoof a caller ID you need to have a PBX (private branch exchange) and have an external trunk to allow calls to go to the outside world. You can obtain a popular free software-based PBX called Asterisk. This software allows you to turn any system into a PBX.
How to communicate externally?
To be able to communicate externally, you will need to obtain access to a VoIP provider. You can purchase the particular services that you need from a VoIP provider online. A prevalent form of communication between the PBX and a VoIP provider is SIP (session initiation protocol). Once the trunk has been purchased and configured, you will be able to communicate with the outside world.
What type of Hardware do you need?
There are many phones that can use SIP to communicate with the VoIP provider. However, for my configuration, I have used two of the Grandstream DP720, and they require the Granstream base station DP750. This base station can be configured to use SIP to communicate with Asterisk that is running on a Raspberry PI 3 B+ using RasPBX.
What is RasPBX?
RasPBX is Asterisk for the Raspberry PI. RasPBX contains Asterisk to be able to function as a PBX and FreePBX for easy configuration of Asterisk. RasPBX contains Debian Stretch as the operating system so that it can function on the Raspberry PI.
How difficult is it to spoof calls with Asterisk?
This requires that Asterisk has been configured to use the VoIP trunk and that the routes have been configured. Asterisk allows for easy configuration of the outbound caller ID. All that needs to be configured to start spoofing outgoing calls is to configure the outbound caller ID field. This field doesn’t have any verification to determine whether or not the system is authorized to use the provided number for the caller ID. However, VoIP providers know what numbers should be expected for the caller ID and can block the use of unauthorized numbers. The VoIP provider that I used did not block unauthorized numbers. It should be noted that spoofing caller IDs for malicious use is prohibited in many countries and that fines can be imposed for malicious use.
Setting the Caller ID

What does a caller ID look like in a packet capture?
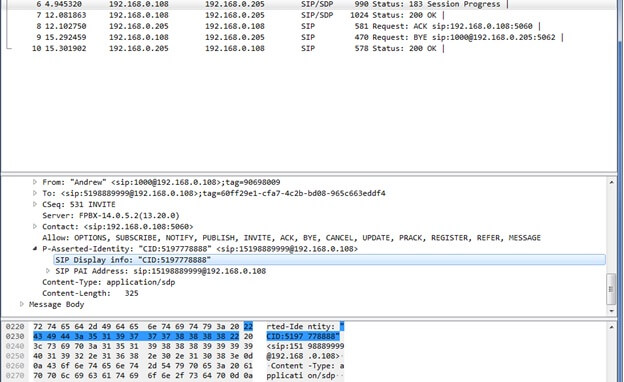
This packet capture demonstrates a call from extension 1000 to an external number using SIP. The internal users know that they can dial 1000 to reach Andrew. However, external users who receive a call from extension 1000 wouldn’t know how to call Andrew back. The session initiation protocol asserts that Andrew is calling from 5197778888. This allows external users to call the number and hopefully reach Andrew. This will not be the case if Andrew didn’t own the number.
Are Asterisk and other PBX systems to be blamed?
PBX systems are not the cause of caller ID spoofing. The PBX itself has not verification for valid caller IDs and even if the owner is authorized to use the configured number. People can use equipment for malicious purposes, and the equipment cannot be blamed for what it is instructed to do. The FCC in the United States is therefore pushing telecommunication providers to verify if the caller is authorized to use the particular number using robust call authentication.
5 Things Your FIM Solution Should Be Doing for You
Discover the pivotal role of File Integrity Monitoring in maintaining system security and compliance with major standards. Tripwire Enterprise stands out as an advanced solution, offering real-time detection and detailed context for system changes, making it a superior choice for robust cybersecurity.

