
The Shamoon attack campaigns have been busy over the past few months. On November 17, 2016, the operation unveiled its second incarnation by targeting an organization in Saudi Arabia with Disttrack wiper malware. Just a few days later, the second wave of Shamoon 2 once again dropped Disttrack on another Saudi Arabian company's network, only this time the malware contained administrator account credentials for accessing and wiping Huawei’s virtualized desktop infrastructure (VDI) products. The operation's third wave came in January 2017 and revealed a potential link between Shamoon 2 and a network reconnaissance campaign.
These attack series made a lot of noise in the security industry, spurring researchers to investigate Shamoon and look for any ties that might link it to other threat actors. Symantec's security responders came up with one possible lead when they discovered another group had compromised at least one administrator computer at the organization which Shamoon targeted on 17 November 2016. This actor, which goes by the name "Greenbug," acted one day prior to Shamoon's deployment of Disttrack and used its own custom program to infect the machine. Here's how Symantec thinks Greenbug operated in that instance and others:
"It is believed that the attacks start with an email that asks the recipient to download a RAR archive containing what is purported to be information about a business proposal. These lure documents were hosted on a legitimate website, which may have been previously compromised by Greenbug. The Ismdoor malware is hidden inside the RAR archive using an alternate data stream."
As of February 2017, researchers at NCC Group had spotted three versions of Ismdoor, Greenbug's signature trojan. All those forms use timer-queue callbacks to initiate execution after a specific timeframe. Known as timing-based evasion, this is one of the most common evasive behaviors employed by malware today. Each iteration of Ismdoor also adds upon the capabilities of its predecessor(s). For instance, whereas the first version has limited functionality, its successor collects information about a target system. A keylogging feature is available in the third variety. In the attack against the Saudi Arabian organization, Ismdoor used HTTP-based communication with its command and control (C&C) server to open a backdoor on the compromised machine. The malware might have also leveraged this communication to infect computers with additional espionage tools. Such activity makes the trojan easy to spot. In fact, RSA developed two queries that allow sysadmins to detect the malware and its C&C communications.
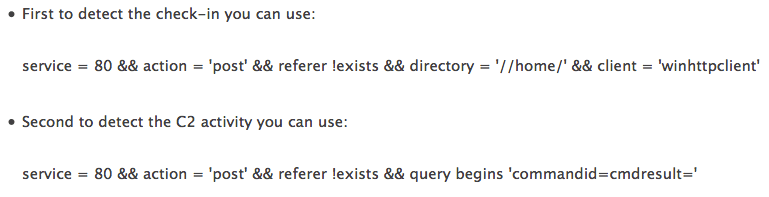
Source: RSA But Ismdoor is still evolving. NCC Group discovered as much when they observed refactoring and changes in the code along with the introduction of versioning in more recent samples. This dynamism helps to explain Arbor Networks' detection of an even newer incarnation of Ismdoor that traded its HTTP C&C communications for a covert channel using AAAA DNS queries for IPv6 addresses. The malware's newest form comes with an encrypted configuration that contains a primary and secondary C&C domain as well as identifiers, timeouts, and flags. (Ismdoor uses a substitution cipher to decrypt the configuration.) Its new and improved C&C mechanism can be divided into three layers. Arbor Networks explains how the first layer, which consists of DNS, works:
"All data sent between the bot and the C2 is done using AAAA DNS UDP queries. Data to the C2 is via specially crafted query names and data from the C2 is returned via IPv6 addresses. The bot side of the connection drives all communications."
The next layer up acts as a transport for the communications, which are split into "sessions" consisting of five DNS requests and replies. Finally, the third layer contains C&C messages, of which there are at least eight. One of these messages, M:GAC?, retrieves bot commands, which enable Ismdoor's handlers to restart itself, upload files, and remove or execute a keylogger, among other functions.
Source: NCC Group When the malware encounters a command that doesn’t match a predefined one, it sends it to a command shell and returns the result. Dennis Schwarz, a research analyst on Arbor's ASERT Team, helped detect Ismdoor's new C&C mechanism and says it reveals the skill level of the malware's operators. He also told The State of Security how organizations can use the new technique to detect the trojan's C&C activity:
"While using the DNS as a malware command and control mechanism isn't new, it is fairly rare in the wild. It sheds light on the technical abilities of an attacker who implements and uses it. While most novice coders can figure out how to send and receive HTTP, it takes a far more advanced coder to build a full-featured communications protocol on top of DNS. Using Ismdoor's DNS is significant for a defender because it is highly unlikely that looking at a bunch of DNS traffic for malware commands and/or data exfiltration is a high priority. These types of covert channels exchange data very slowly over many DNS requests and replies, and it is easy to overlook. "The good news with regard to Ismdoor's DNS traffic is that when it sends data to the command and control server it will very likely send invalid characters (e.g. !, &, @) in the subdomains it generates. For example, one of the subdomains from the blog post looks like: TTpDQz8!.0.dr.237735C7DCF34DE59F8E04CB852401B3.malicious.com It contains an '!' character which isn't an allowed character in legitimate subdomains. The attacker's command and control server doesn't care because it is expecting characters like this, but you wouldn’t see these types of domains in benign traffic."
While organizations remain on the lookout for invalid characters in the subdomains generated by the malware, Arbor Networks and others will continue to research possible ties linking Ismdoor and Greenbug to Shamoon. There's no definitive connection yet. But as VirusTotal received all known samples of the DNS variant of Ismdoor from Saudi Arabia--the same region that suffered the Shamoon 2 attacks--researchers could establish a link very soon.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

