
Industrial control system (ICS) security is a growing concern for organizations around the world. On the one hand, research suggests that vulnerabilities and exposures are increasingly jeopardizing the security of ICS assets. In their report Overload: Critical Lessons from 15 Years of ICS Vulnerabilities, the FireEye iSIGHT threat intelligence team tracked 1,552 ICS vulnerabilities from January 2000 through April 2016. Those types of security issues appear to be growing more numerous over time. FireEye iSIGHT found that 90 percent of ICS flaws occurred after 2011, with a 49 percent increase in disclosures observed between 2014 and 2015. On the other hand, industrial control systems are known to be vulnerable to types of attacks that threaten traditional IT assets. The United States Department of Homeland Security’s Industrial Control System Cyber Emergency Response Team (ICS-CERT) tracked 295 security incidents involving critical infrastructure in 2015. As Tripwire senior product marketing manager Kathy Trahan explains in a blog post, a number of those incidents had something in common:
"Not surprisingly, spear phishing tactics were cited as the single most common attack method. A vendor’s research arrived at the same findings. Spear phishing is a people issue that suggests everyone needs to know about cyber security."
Spear phishing poses a serious threat to industrial control systems. Each day, computer criminals leverage this social engineering technique to develop increasingly sophisticated attacks against all types of organizations, including those in the industrial sector. Unfortunately, it looks like one of their latest campaigns is a real doozy. Kaspersky Lab senior security researcher Mohamad Amin Hasbini says the campaign, dubbed "Operation Ghoul," began back in March 2015 but churned out a series of new attack waves on 8 June 2016 and 27 June 2016:
"These have been highly active in the Middle East region and unveiled ongoing targeted attacks in multiple regions. The attackers try to lure targets through spear phishing emails that include compressed executables. The malware collects all data such as passwords, keystrokes and screenshots, then sends it to the attackers."
As Tripwire's Maritza Santillan mentioned on 17 August, the campaign begins when a target receives a spear phishing email claiming to originate from the Emirates NBD, a bank based in the United Arab Emirates. The email comes with a .7z attachment that says it's a payment document.
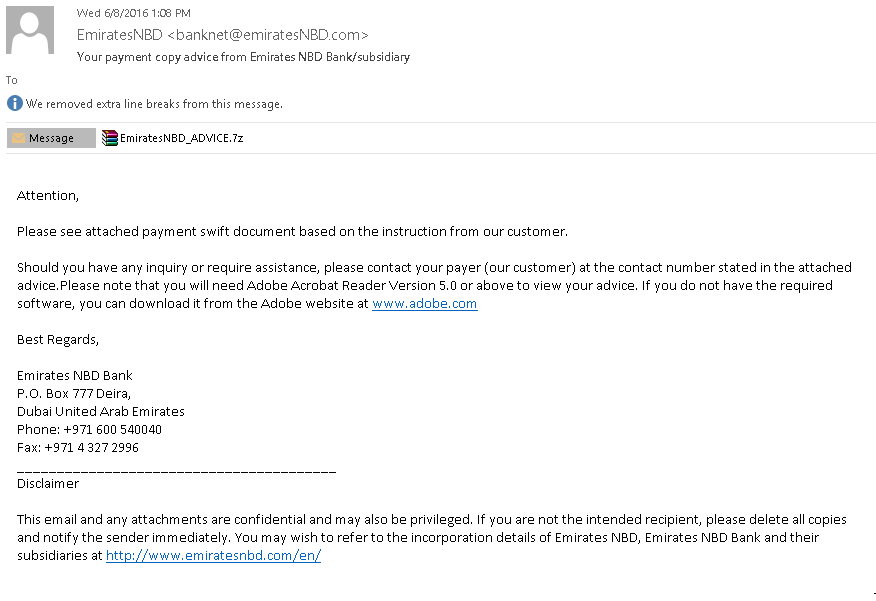
Source: Kaspersky Lab It's not. In reality, the attachment is laden with malware based on Hawkeye (also known as KeyBase), spyware which other fraudsters have incorporated into their Nigerian payment diversion scams.
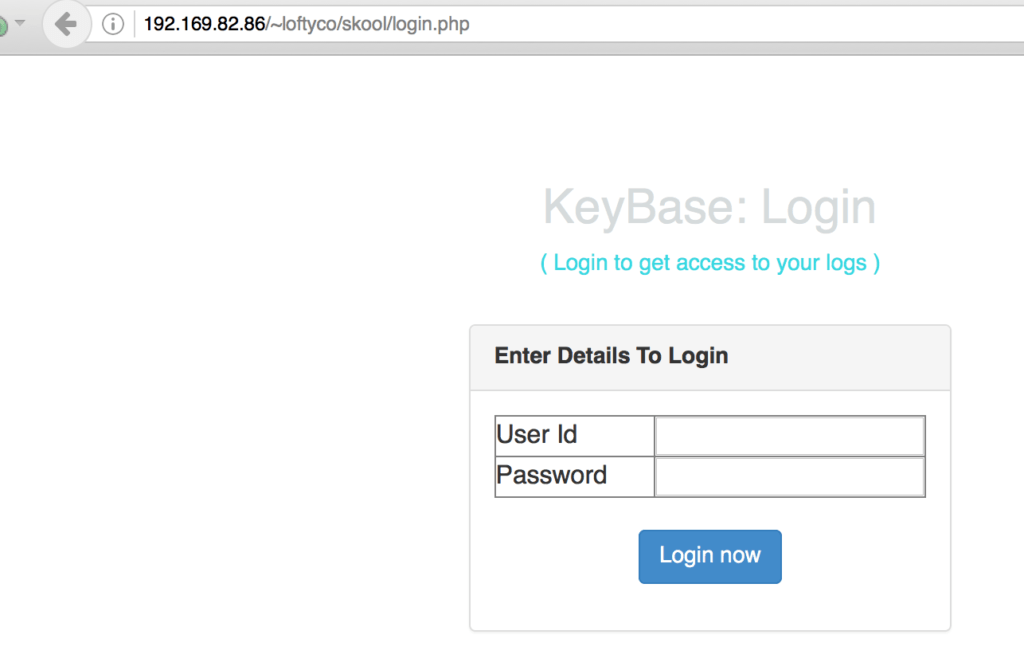
Source: Kaspersky Lab Attackers use the malware to capture a victim's keystrokes, clipboard data, and data from local browsers, among other pieces of information. They then exfiltrate their haul via HTTP to two servers located at ozlercelikkapi[.]com and eminenture[.]com. In total, more than 130 organizations are believed to have fallen victim to the spear phishing campaign so far. Spain had the largest number of victims at 25 organizations, followed by Pakistan (22), the United Arab Emirates (19), India (17), Egypt (16), and others.
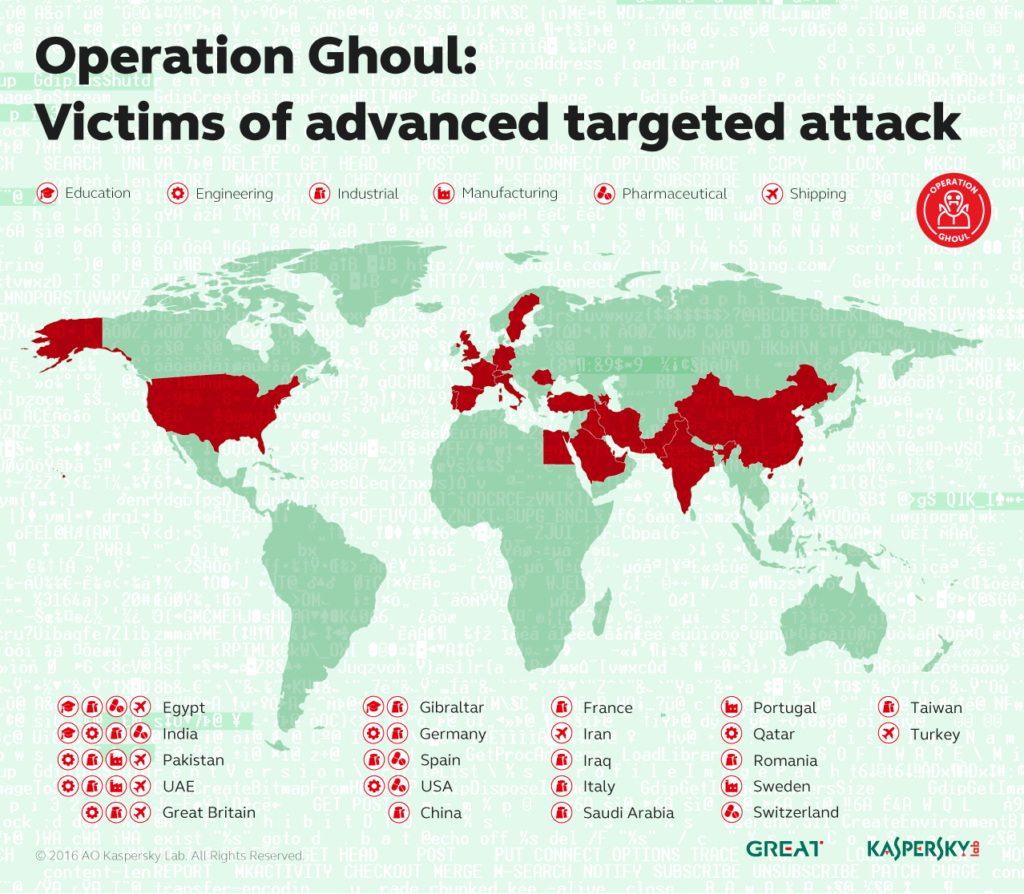
Source: Kaspersky Lab Hasbini explains that victims have overwhelmingly belonged to the petrochemical, naval, military, aerospace, heavy machinery, solar energy, steel, pumps, and plastics industries:
"Operation Ghoul is one of the many attacks in the wild targeting industrial, manufacturing and engineering organizations…[.] Kaspersky Lab recommends users to be extra cautious while checking and opening emails and attachments. In addition, privileged users need to be well trained and ready to deal with cyber threats; failure in this is, in most cases, the cause behind private or corporate data leakage, reputation and financial loss."
For more information on Operation Ghoul, read Kaspersky Lab's report here. To learn more about how you can protect your ICS systems against spear phishing attacks and other threats, please check out the resources below:

