
Point-of-sale (POS) malware activity, specifically network traffic for data exfiltration, quadrupled over Thanksgiving weekend. For their ongoing threat analysis, researchers at Proofpoint use network sensors deployed by its Emerging Threats group to track POS malware contact with command and control (C&C) servers. They had expected increased traffic with Black Friday. But what they ultimately saw around Thanksgiving was nothing less than dramatic. As the team explains in a blog post:
"While Figure 1 shows occasional spikes with a regular ebb and flow of network activity for several POS malware families, Proofpoint researchers observed 3-4x increases in data exfiltration traffic related to ZeusPOS and NewPOSthings variants over the Thanksgiving weekend.
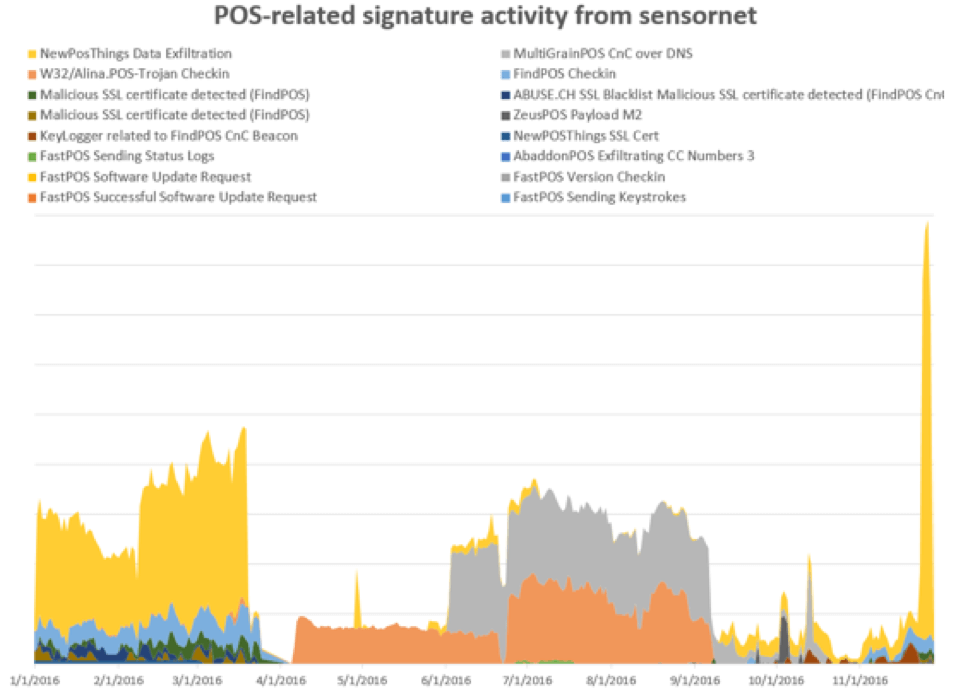
Figure 1: Top POS malware by indexed volume of network activity (Source: Proofpoint) Researchers at the Sunnyvale-based security firm wanted additional insight into POS malware behavior. They therefore decided to look at traffic patterns from the beginning of the year. Not only did the team find that most POS malware activity revolves around a few dominant variants. It also observed major players sharing infrastructure with one another, something that other baddies like Dridex and Locky also do.
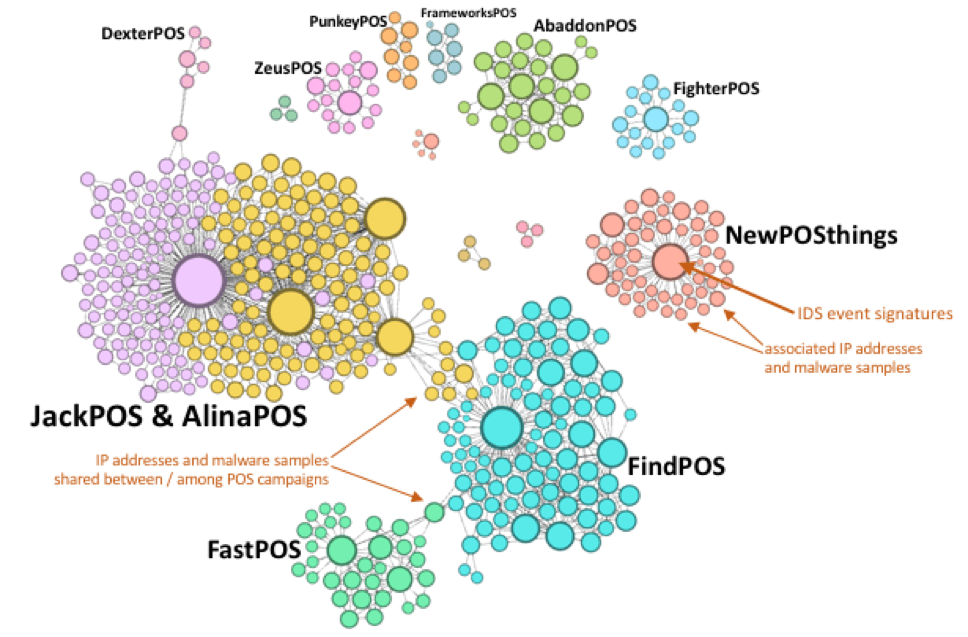
Figure 4: Network graph showing relative activity and connections by POS malware family (Source: Proofpoint) To achieve even more insight, Proofpoint's researchers also examined several POS malware campaigns on an individual basis. Here's what they learned about the AbbadonPOS variant, for instance:
"The 'personalized actor' or TA530 frequently engages in small to medium-sized campaigns that involve personalized emails and lures to increase their effectiveness. We observed campaigns from this actor targeting big-box retailers and grocery chains in July and October. The attacks involved thousands of messages dropping AbaddonPOS via TinyLoader. The attacker uses a personalized 'client feedback' email with the recipient's name in the subject, attachment name, and email body that references a specific store location.... This creates a socially engineered, legitimate-looking lure that entices users to open an attached Word document and enable macros. Enabling macros installs TinyLoader which in turn installs AbaddonPOS."
These and other campaigns indicate bad actors are increasingly using personalization, social engineering techniques, and diverse means of distribution to deliver POS malware to organizations. Companies working towards PCI compliance must therefore make an effort to protect customers against that growing threat. They can do so by investing in a solution that's capable of detecting POS threats in real-time.

