
A free tool called RansomFree that helps protect computers and servers running Windows against ransomware is now available for download. Boston security firm Cybereason developed its tool to respond to the evolution of ransomware, including the ability of most crypto-malware to bypass anti-virus solutions. As Cybereason Labs researcher Uri Sternfeld explains in a blog post:
"...[R]ansomware-on-demand services and self-modifying code easily generate completely new code with the same functionality, making this detection method obsolete. The ransomware distribution system described by Cybereason in its Operation Kofer research is just one example of an attack where each victim was infected with a unique ransomware binary. In addition, ransomware is the preferred payload for drive-by download and malvertising campaigns. Both of these attacks infect victims without their knowledge, and unfortunately, spam filters and sandbox email scanning systems cannot prevent them."
The security firm has analyzed tens of thousands of variants of over 40 ransomware families including Locky, CryptoWall, TeslaCrypt, and Cerber. Most of those samples behave in a similar fashion: low-level file encryption. Cybereason therefore developed its utility so that it could detect ransomware by what it does and not by its signature. According to a test performed by Lawrence Abrams of Bleeping Computer, RansomFree works by creating a number of randomly named folders throughout a computer that act as honeypots. Those folders start with symbols like "$" and "!," which ensures ransomware would scan them first.
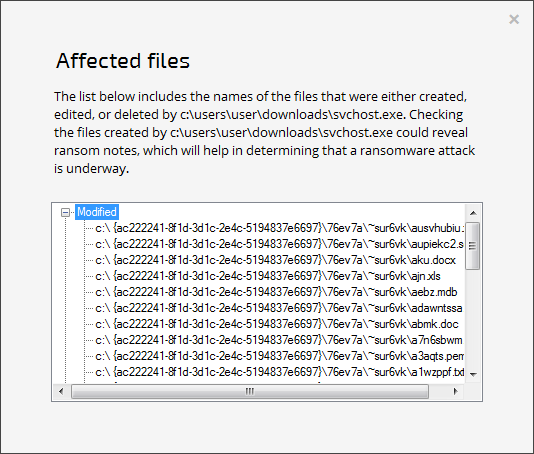
A list of files RansomFree detected as targeted by an encryption-heavy process (Source: Bleeping Computer) The tool monitors the integrity of those files. If it detects an encryption-heavy process, it pauses it and shows a prompt to the user asking them to stop the process or allow it to continue. Please click the demo video below to see Cybereason's utility in action. https://youtu.be/nr1w2mrOpto RansomFree is reactive, meaning it can't detect ransomware before it's already begun encrypting a victim's files. If even one encrypted file isn't good enough for a user, they should complement RansomFree with a robust data recovery strategy that involves both local and cloud-based backups. Users should also learn more about how they can prevent a ransomware infection.

