
The HookAds malvertising campaign redirects users to a landing page for the RIG exploit kit that comes prepackaged with all types of baddies. HookAds, which got its name from a string found by Malwarebytes researchers in the delivery URL, works as follows. A malvertising chain redirects visitors to adult websites that sometimes generate millions of views a month to a secondary site. There, a third-party server analyzes the traffic to determine whether the victim is a target. If they aren't, the server displays a regular ad banner that redirects the visitor to other adult websites. If they are, it loads up a fake ad banner with a malicious script instead.
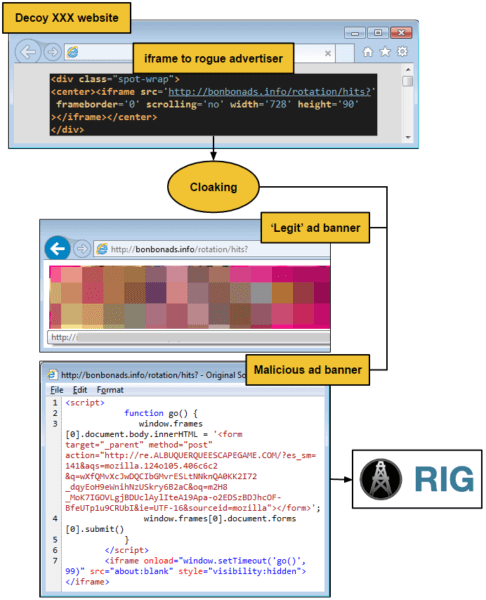
Source: Malwarebytes Jérôme Segura of Malwarebytes has spotted dozens of rogue ad domains participating in this campaign. As he explains in a blog post:
"The fake ad server infrastructure grew during the past few months and our honeypots caught 3 sequential IP addresses that host over a hundred rogue ad domains. All of these domains have been registered with the intention of looking like advertising platforms. While some domains were used for long periods of time, most switched every day or so to let a new one in."
All fake ads that come with that malicious script redirect to one location: a landing page for the RIG exploit kit. For this campaign, the malicious software package comes with the ability to exploit a vulnerability in Adobe Flash Player. That particular exploit code is protected by SWFLOCK, online technology which provides code obfuscation and encryption for Flash files.
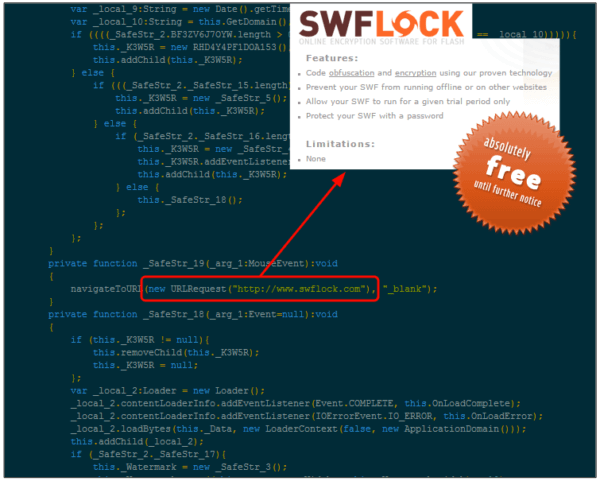
Source: Malwarebytes In the event RIG finds a Flash vulnerability or other bug it can exploit, it drops CrypMic ransomware or a number of other malicious payloads onto the victim's computer. Segura explains users are still at risk of HookAds as of this writing:
"The HookAds malvertising campaign is still running at the time of writing this post, with new rogue ad domains getting registered each day. We are blocking the malicious IP range to protect our customers and Malwarebytes Anti-Exploit users are also shielded against the RIG exploit kit."
Users can protect themselves by making sure RIG finds no open security holes on their systems. That means they should implement all software updates as soon as they become available and maintain an up-to-date anti-virus solution on their computers.

