Change is prolific in organizations’ IT environments. Hardware assets change. Software programs change. Configuration states change. Some of these modifications are authorized insofar as they occur during an organization’s regular patching cycle, while others cause concern by popping up unexpectedly.
Organizations commonly respond to this dynamism by investing in asset discovery and secure configuration management (SCM). These foundational controls allow companies to build an inventory of approved devices and monitor those products’ configurations. Even so, companies are left with an important challenge: reconciling change in important files. For that challenge, many enterprises are turning to file integrity monitoring (FIM).
What Exactly Is File Integrity Monitoring?
File integrity monitoring (FIM) is a technology that monitors and detects file changes that could be indicative of a cyberattack. Otherwise known as change monitoring, FIM specifically involves examining files and other systems to see if and when they change, how they change, who changed them, and what can be done to restore those files if those modifications are unauthorized.
FIM is both a technology and a cybersecurity process. FIM solutions continuously check for changes across files, operating systems, servers, and other assets in the digital environment that regularly incur change. It is a critical process for the success of any cybersecurity program, as it’s the only security control focused on proactively catching unexpected changes. Those unexpected changes could be the result of tampering by cybercriminals or human error. Simply put, FIM is the cybersecurity process that manages the integrity of an organization’s digital environment.
3 Advantages of Running a Successful File Integrity Monitoring Program
- Protect IT Infrastructure: FIM solutions monitor file changes on servers, databases, network devices, directory servers, applications, cloud environments, and virtual images to alert you to unauthorized changes.
- Reduce Noise: A strong FIM solution uses change intelligence to only notify you when needed—along with business context and remediation steps. Look for detailed security metrics and dashboarding in your FIM solution.
- Stay Compliant: FIM helps you meet many regulatory compliance standards like PCI-DSS, NERC CIP, FISMA, SOX, NIST and HIPAA, as well as best practice frameworks like the CIS security benchmarks.
Why Is File Integrity Monitoring Important?
File integrity monitoring was invented in part by Tripwire founder Gene Kim. From there, it went on to become the security control around which many organizations now build their cybersecurity programs. The specific term “file integrity monitoring” itself was widely popularized by the PCI standard. Companies can leverage the control to supervise static files for suspicious modifications such as adjustments to their IP stack and email client configuration. As such, FIM is useful for detecting malware as well as achieving compliance with regulations like the Payment Card Industry Data Security Standard (PCI DSS). Aside from the importance of compliance, FIM also helps organizations minimize unauthorized changes in ephemerally-connected endpoints such as remote workstations, which have become increasingly prolific since the onset of the COVID-19 pandemic.
File Integrity Monitoring Use Cases
FIM is applicable in a number of security and compliance use cases because of its primary function of detecting unauthorized change. It ebables organizations to differentiate between "good" and "bad" changes in their digital environments to stop potential breaches before cyberattacks can succeed. Change visibility is crucial because every security breach begins with a single change.
Detecting Change in Complex Enterprise IT
A small alteration to one file can expose your whole network to a potential attack. File integrity monitoring, in its simplest sense, is about keeping track of change from an established baseline and alerting you to any unexpected change that may represent a security risk or a compromise in regulatory compliance. For example, an energy utility provider might use a FIM solution to automate change detection in order to avoid costly unplanned downtime.
Comparing Against a Secure Baseline
In order to know which file changes are relevant to your security, you must first establish an authoritative data integrity baseline. A FIM solution like Tripwire File Integrity Manager will capture your system’s configuration baseline and deliver the “who, what, and when” details of each relevant file change — all without bogging you down in notifications about routine changes.
Simplifying Compliance Audits
FIM makes audits easier by providing a clear "paper trail" of compliance alignment over time. For example, an organization might use a FIM solution to monitor their in-scope assets for PCI across their operating systems, databases, servers, and other assets. Applying PCI content to those assets will reveal their level of compliance alignment, and an advanced FIM solution will supply step-by-step guidance needed to remediate instances of noncompliance. Then when it comes time for their audit, they will be able to provide documentation of these efforts to their auditor to demonstrate their compliance program's efficacy.
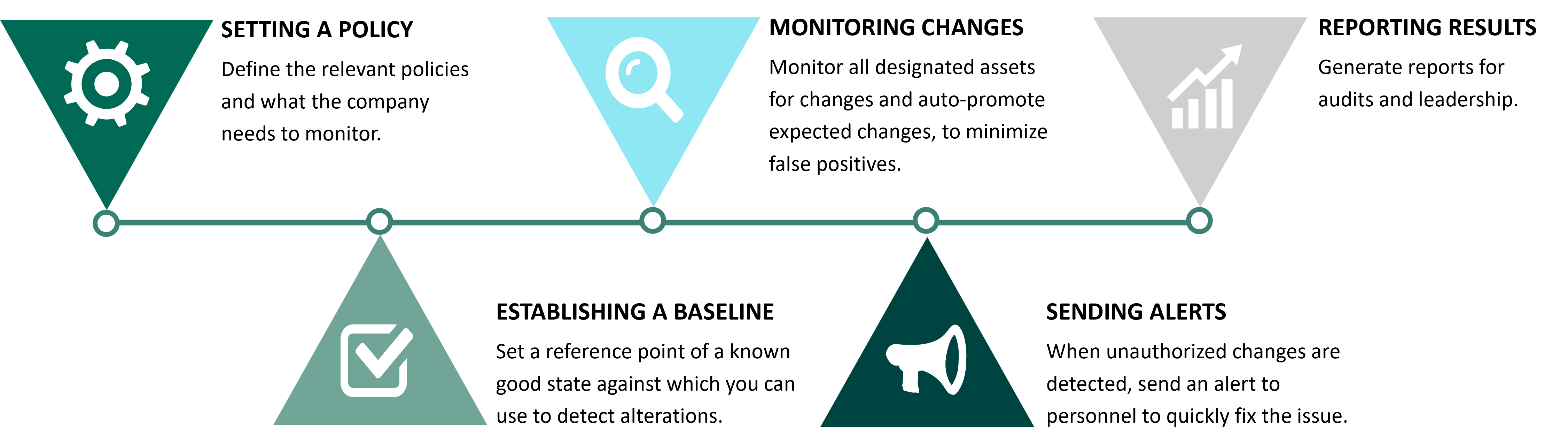
How File Integrity Monitoring Works (in 5 Steps)
There are five steps to file integrity monitoring:
1. Setting a policy
FIM begins when an organization defines a relevant policy. This step involves identifying which files on which computers the company needs to monitor.
2. Establishing a baseline for files
Before they can actively monitor files for changes, organizations need a reference point against which they can use to detect alterations. Companies should therefore document a baseline, or a known good state for files that will fall under their FIM policy. This standard should take into account the version, creation date, modification date, and other data that can help IT professionals provide assurance that the file is legitimate going forward.
3. Monitoring changes
With a detailed baseline, enterprises can proceed to monitor all designated files for changes. They can augment their monitoring processes by auto-promoting expected changes, thereby minimizing instances of false positives.
4. Sending an alert
If their file integrity monitoring solution detects an unauthorized change, those responsible for the process should send out an alert to the relevant personnel so that they can quickly fix the issue.
5. Reporting results
Sometimes, companies use FIM tools for ensuring PCI DSS compliance. In that event, organizations might need to generate reports for audits in order to substantiate the deployment of their file integrity monitoring assessor.
4 Things to Look for When Assessing File Integrity Monitoring Tools
Unfortunately, for many organizations, FIM mostly means noise that complicates the work of security personnel. Too many changes, no context around these changes, and very little insight into whether the changes actually pose force security teams into a position where they need to investigate which changes relate to one another. In the process, these professionals could waste their time looking into false positives, thus contributing to a sentiment of alert fatigue that leaves organizations exposed to data breaches and other digital threats.
This highlights the reality of FIM. It is a critical security control, but it must provide sufficient insight and actionable intelligence for organizations to augment their security postures.
To complement the phases described above, organizations should look for additional features in their file integrity monitoring solution. That functionality should include, for example, a lightweight agent that can toggle “on” and “off” and that can accommodate additional functions when necessary. The solution should also come with total control over a FIM policy. Such visibility should incorporate:
Management
The solution should come with built-in policy customizations.
Granularity
The product should be capable of supporting different policies according to the types of devices that fall within the scope of an enterprise FIM program.
Editing
Organizations should have the ability to revise a policy according to their evolving security requirements.
Updates
All systems should quickly update via content downloads.
 The FIM Software Buyer's Guide
The FIM Software Buyer's Guide
Find out which type of FIM solution would be best suited for your organization’s security needs.
File Integrity Monitoring With Tripwire
Tripwire’s file integrity monitoring solution focuses on adding business context to data for all changes that occur in an organization’s environment. As such, it provides IT and security teams with real-time intelligence that they can use to identify incidents that are of real concern. It also helps personnel learn the who, what, when, and how of a change, data which they can use to validate planned modifications.
Learn More About Tripwire and FIM
Please download the white paper FIM Isn’t Just for Files Anymore for information on other core security measures of interest. You can also see Tripwire’s file integrity monitoring tool in action by watching the video posted below.
Part of a Broader Security Effort
File integrity monitoring is just one of the foundational controls for which organizations should look when purchasing a new solution. To learn how Tripwire’s tools can help your organization implement those other security measures, click here.
File Integrity Monitoring Software Buyer's Guide
Selecting the appropriate File Integrity Monitoring solution is crucial for organizational security. Tripwire's comprehensive buyer's guide covers all aspects of FIM, including operational requirements, integration, and reporting. Find the best FIM solution to meet your organization's specific security needs.

