
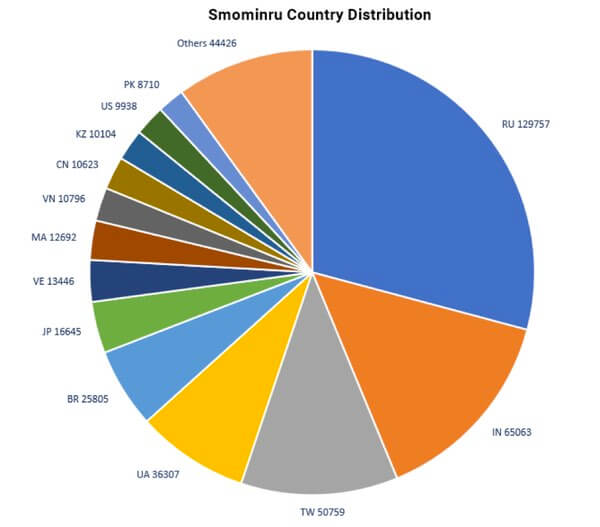
Why go to all the bother of writing ransomware that demands victims pay a Bitcoin ransom? If all you want is cryptocurrency, why not use the infected computers to mine the crypto coins themselves? That way you don't have to rely on a human victim buying some Bitcoin, and nervously making their way onto the dark web to make their ransom payment. According to security researchers at Proofpoint, that's exactly the reasoning shown by online criminals who are moving from regular ransomware to cryptomining. A Monero-mining botnet called Smominru is said to have infected 526,000 Windows PCs since May 2017 - mostly in Russia, India, and Taiwan - and is earning millions of dollars for its operators.
How has Sominru managed to hijack so many computers into secretly mining cryptocurrency? Through use of the notorious EternalBlue exploit (CVE-2017-0144), stolen from the National Security Agency (NSA) by the ShadowBrokers hacking group, and then most famously put to work by the hard-hitting WannaCry ransomware. Smominru isn't the only threat. As researchers at Talos report, cryptomining may be taking over from ransomware as weapon of choice for cybercriminals:
"The number of ways adversaries are delivering miners to end users is staggering. It is reminiscent of the explosion of ransomware we saw several years ago. This is indicative of a major shift in the types of payloads adversaries are trying to deliver. It helps show that the effectiveness of ransomware as a payload is limited. It will always be effective to ransom specific organizations or to use in targeted attacks, but as a payload to compromise random victims its reach definitely has limits. At some point the pool of potential victims becomes too small to generate the revenue expected."
Although it is unlikely that any individual infected PC will generate significant amounts of money for cryptominers, when you have hundreds of thousands of hijacked PCs under the command of a botnet the profits to be made are considerable. Furthermore, a cryptomining attack has an arguably longer shelf-life than a ransomware attack. By its very nature, a traditional ransomware attack has to announce its presence to its victims in order to request a payment. Cryptominers, in contrast, want to draw as little attention to themselves in order to mine for as long as possible to generate the maximum income. In fact, the biggest clue that most users will have that their computers may be affected by a cryptominer is if they found the PC is slowing down, its battery running out at a quicker rate, or the fan blowing at full blast. Don't make the mistake of thinking that this is a victimless crime. If your computers get recruited into a cryptomining botnet like Smominru, it's your electricity and computer power that is being stolen. Keep your computers up-to-date with security patches, defended with layered security solutions, and your wits about you. Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.

