
Attackers have lots of ways of gaining access to a target's information. One of their preferred attack vectors is exploiting careless end user behavior. This is especially true when it comes to users who don't adequately protect their web accounts. For instance, bad actors targeted users of TeamViewer, software which allows IT professionals to gain remote desktop access, on two separate occasions in the first half of 2016. In both incidents, observers thought someone had hacked TeamViewer or that the company had not implemented adequate security measures. But the company revealed that careless behavior, i.e. users reusing weak passwords across their accounts, had helped attackers gain access to victims' computers. Nothing had happened with TeamViewer itself. The same can be said about TeamSpy. First discovered in 2013, TeamSpy is a piece of malware that uses TeamViewer software, which like many applications loads external code known as Dynamic Link Libraries (DLLs). The malware works by implementing a technique known as DLL Hijacking. This involves tricking the TeamViewer application loader into executing malicious code. The CrySyS Lab elaborates on the attack in a report (PDF):
"The attackers install an original, legitimate TeamViewer instance on the victim computer, but they modify its behavior with DLL hijacking, and they obtain remote access to the victim computers in real-time. Therefore, the attackers are not only able to remotely observe the infected computers, but they can also misuse TeamViewer to install other tools to obtain important information, files, and other data from the victim."
DLL Hijacking is possible with applications depending on how they call DLLs. This doesn't mean the affected applications are inherently unsafe, however. On the contrary, the technique oftentimes works if and only if attackers trick users into downloading a malicious DLL onto their computers first. Bad actors usually turn to social engineering techniques for that purpose. Case and point, Heimdal Security recently discovered an attack campaign that leverages email spam to infect users with TeamSpy. Let's dive into the specifics of this operation.
TeamSpy Email Spam
The attack begins when a user receives an email from a spoofed return address. Most of the time, the subject line has something to do with an eFax message. The attachment, "Fax_02755665224.zip," reinforces this ploy. But the attachment is not what it appears to be. As Heimdal's security evangelist Andra Zaharia explains in a blog post:
"The attached file is a zip file, which, when opened, triggers the accompanying .exe file to be activated. This causes for the malicious TeamSpy code to be dropped onto the victim’s computer, as a malicious DLL: "[% APPDATA%] \ SysplanNT \ MSIMG32.dll. That library then recorded via C: \ Windows \ system32 \ regsvr32. exe “/ s” [% APPDATA%] \ SysplanNT \ MSIMG32.dll"
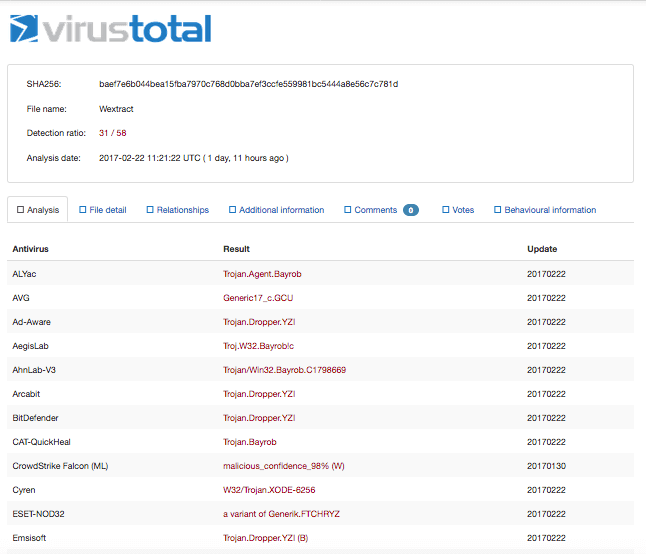
Once activated, TeamSpy loads up a keylogger. This component collects a victim's usernames and passwords, assembles it into a file, and continuously sends it to its command and control (C&C) server. Meanwhile, the victim remains oblivious to the hidden TeamViewer session that powers TeamSpy. The attack, which can circumvent various security protections including two-step verification (2SV), has a 31/58 VirusTotal detection rating as of 22 February 2017.
The Need for Security Awareness
Reflecting on the TeamSpy email attack, Heimdal's CEO Morten Kjærsgaard feels organizations need to invest in security awareness:
"This type of attack, as many others that use similar tactics, highlights (once again) how critical basic cyber security education is. Cyber hygiene, as we call it, is fundamental to our lives, as we can no longer draw a clear line between our online and our 'offline' lives."
In Kjærsgaard's mind, this means knowing four things:
- Which emails to open and which to mark as spam.
- Which email attachments to avoid and never touch.
- The main tactics that cybercriminals use to infect your computer.
- How psychological manipulation is part of every attack.
By familiarizing themselves with security best practices, users can take their digital security into their own hands and choose tools that are designed to protect their data. They can also watch out for future attack campaigns like the TeamSpy operation explained above.

