
Tripwire is pleased to announce the release of its newest infographic, “Where Are Your Cyberattacks Coming From?” Created in response to the release of Verizon’s 2015 Data Breach Investigations Report (DBIR 2015) back in April, the infographic explains the five most common attack patterns behind today’s data breaches. In this article, I will review each of these methods, identify which industries are most vulnerable to each pattern of attack, and identify real-world examples for each attack type.
Attack Pattern #1: Web applications (9.4% of incidents)
This year, the authors of the DBIR 2015 noticed that organized crime has become the most frequently seen actor behind web application attacks. These computer criminal syndicates, as well as other malicious actors, have shifted their tactics to embrace Strategic Web Compromise, in which attackers target a web server simply to set up an attack against a different target. Two-thirds of web app attacks now embrace this secondary style attack, with the vast majority (98%) of them constituting opportunistic campaigns against easy targets. Further analysis reveals that in the financial sector, 82% of web application attacks back in 2014 involved end-user devices, and a tenth incorporated at least one phishing/social engineering element. Attackers in this industry are also getting more creative with their tactics. For example, earlier this year, it was reported that a group of criminals compromised a financial firm’s web application, used that unauthorized access to encrypt a database managed by the enterprise, and eventually demanded $50,000 in return for the decryption key in what has become one of the first publicized “ransomweb” attacks. The information services industry was similarly hard-hit by web application attacks last year. From a more general perspective, approximately 95% of attacks targeting web applications harvested credentials from users’ devices and used this stolen information to compromise their accounts. This trend has somewhat eclipsed cross-site scripting (XSS) and SQL injection, techniques which are still popular among malicious hackers but together constitute just over a quarter of web app attacks.
Attack Pattern #2: Privilege Misuse (10.6% of incidents)
Today, privilege misuse accounts for the top action (55% of incidents) with respect to internal actor breaches. 40% of these incidents were propelled by financial gain and/or convenience, motives that ultimately led internal attackers to either sell the data or use it to directly compete with the victim organization following the breach. For the first time since 2011, cashiers did not top the charts for internal actors most associated with privilege misuse breaches. End users instead ranked number 1 at 37.6% of incidents. They were followed by cashiers at 16.8% and finance at 11.2%. Privilege misuse breaches affect the mining, administrative, and healthcare industries most. However, that does not mean other industries are not vulnerable. Serious privilege escalation bugs were discovered in both Microsoft Windows and all Android devices below Lollipop 5.0 in the past year, which together left potentially hundreds of millions of users vulnerable to an internal security breach. As of this writing, no incidents have resulted from the disclosure of those two vulnerabilities.
Attack Pattern #3: Cyber espionage (18% of incidents)
548 separate incidents of cyber espionage were observed in 2014. Of this total, only one-third had any attribution information available to security researchers and forensic investigators whatsoever. The manufacturing, public, and professional industries were most affected by this method of attack at 27.4%, 20.2%, and 13.3% respectively. The information services industry registered at 6.2% of the total number of cyber espionage incidents, whereas the financial and healthcare sectors measured a combined 1.5%. Further analysis reveals that the preferred medium for this method of attack was malicious email attachments at 39.9%. This was followed by email links (37.4%) and web drive-by attacks (16.6%). In general, trade secrets made up the bulk (85.8%) of information targeted by cyber espionage campaigns, whereas credentials and internal data were stolen in significantly fewer events at 11.4% and 8.5%, respectively. It is important to note that cyber espionage is a tactic reserved not just for computer criminal rings and hacker groups. Nation states have also increasingly embraced this attack pattern, as is evident in the use of Turla malware by a country (most likely Russia) to spy on government institutions, embassies, military installations and other organizations in more than 45 countries, as well as the activities of the Equation Group threat actor.
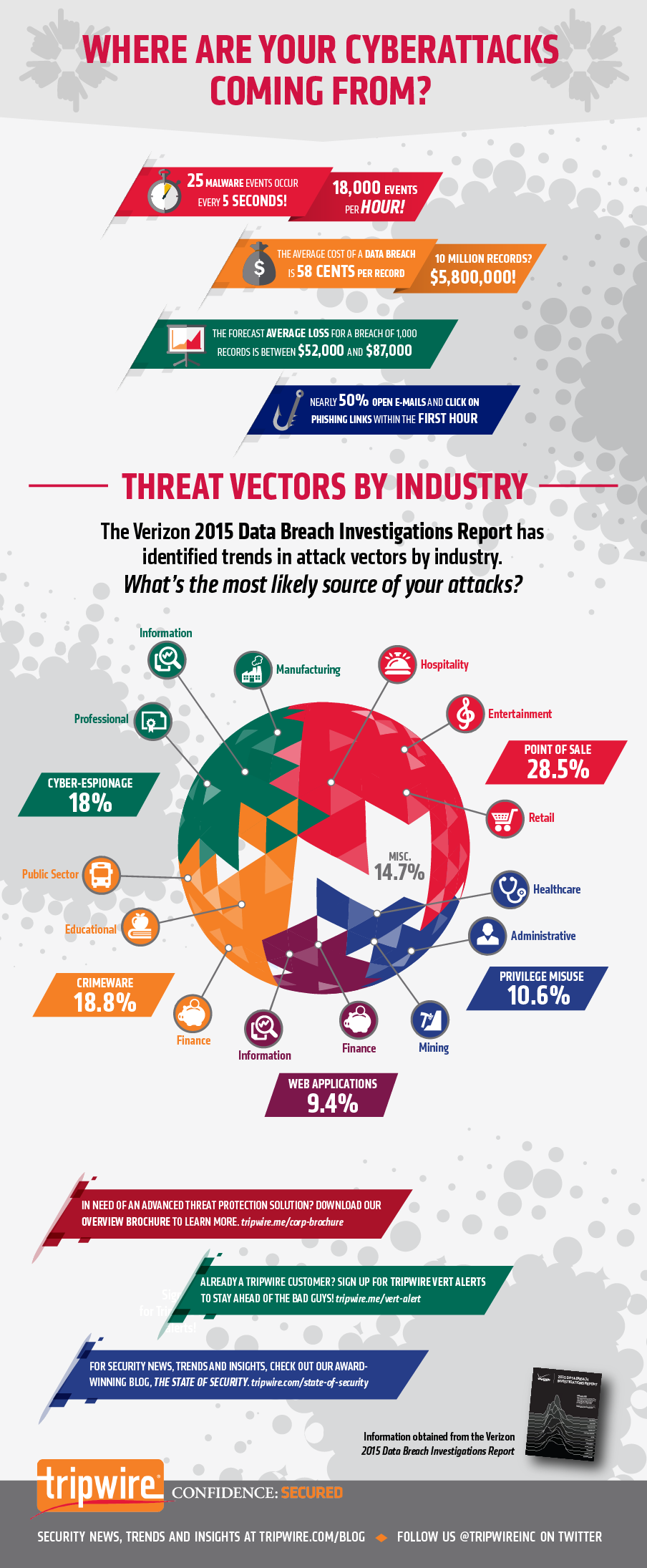
Attack Pattern #4: Crimeware (18.8% of incidents)
Crimeware, or malware infections that do not fit with more specialized classification patterns, such as cyber espionage or privilege misuse, saw command-and-control (C2) malware at the top of the attack pattern at 84.4% of incidents this past year. Denial of service (DoS) attacks came in at 65.4%, marking a jump from eighth to second place. Meanwhile, backdoor compromises represented a little more than a tenth (10.5%) of this particular threat variety. Generally opportunistic and financially motivated in nature, crimeware attacks compromised bank information in more than a half (59.6%) of incidents. This was followed by credentials and personal information at 29.6% and 18.4%, respectively. However, credentials traded places for the top spot whenever a data breach was confirmed, as keyloggers (and hence stolen credentials) were often used to compromise banking data. Significantly, trade secrets were also compromised by this attack pattern in more than one incident, including in the public, educational, and finance industries. Clearly, normal malware can look to steal secrets and not be a part of cyber espionage campaigns. This makes crimeware kits, including Rombertik (Carbon Grabber) and the BlackHole exploit kit, a popular product on the underground market.
Attack Pattern #5: Point-of-Sale (28.5% of incidents)
Perhaps the most common attack pattern with respect to data breaches in 2014 was point-of-sale (PoS) intrusions. This threat variety has seen an evolution in tactics from simple storage scraping to active RAM scraping in recent years, as well as a shift from exploiting default credentials to stealing user credentials. Most of today’s PoS attacks also involve an element of social engineering and were not opportunistic in nature. PoS breaches did affect small and large organizations the same. In the case of the former, attackers directly targeted the PoS device, at which point they then guessed or brute-forced the passwords, whereas for the latter, PoS intrusions consisted of multidimensional attacks that often succeeded in breaching another element of an organization’s computer infrastructure before targeting the PoS system, as was the case with Target. For both large and small enterprises, however, sometimes PoS device vendors were the source of the attack after it was discovered that keyloggers were installed on their products. The hospitality, entertainment, and retail industries were most affected by PoS intrusions.
Conclusion
As our infographic demonstrates, organizations today face the pressure of defending against a variety of attack vectors. These threats emphasize the importance of adhering to basic security standards at minimum and pursuing more sophisticated solutions if the resources are available. For more recommendations on how organizations can protect themselves against today’s threats, please refer to the DBIR 2015 here. Title image courtesy of ShutterStock
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

