
Attackers abused the website of a Ukraine-based accounting software developer to serve banking malware to unsuspecting users. The attack occurred in August 2017 around the Independence Day holiday in Ukraine. At around that time, unknown individuals hacked the website for Crystal Finance Millennium (CFM), a Ukrainian company which provides accounting software along with other services. Those bad actors subsequently leveraged their unauthorized access to host all kinds of malware, including the Smoke Loader downloader and PSCrypt ransomware. It's not clear just how the malefactors compromised CFM's website. Their method of attack isn't a new one, however. As Cisco's Talos researchers explain:
Websites being compromised to serve malicious content is common and it appears that CFM's website was leveraged in the same way. This can be achieved through exploitation of existing vulnerabilities in server-side software or brute-forcing weak credentials, allowing attackers to gain remote administrative access. The fact that it is an accounting software company in Ukraine and the timing of the attack increased visibility.
CFM isn't the first Ukrainian accounting software company to suffer a compromise in recent history, after all. In June 2017, researchers discovered that MeDoc, a small Ukrainian financial technology company which also makes accounting software, experienced a hack through which attackers gained access to its update servers. The nefarious individuals then used those servers to push out a software update infected with NotPetya. That wiper malware spread to other machines using EternalBlue, the same Microsoft vulnerability exploited by WannaCry ransomware less than two months previously. Unlike MeDoc, bad actors didn't compromise CFM's update servers. They used the firm's website only to distribute malware retrieved from malware downloaders as part of an email spam campaign. The accounting software company's website was just one of the domains used to host the malware payload.
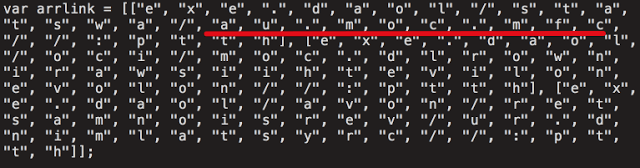
Downloader Code Snippet (Source: Cisco's Talos) In this particular instance, the downloader retrieved Chthonic, a derivative of the ZeuS banking trojan. The malware first performs several checks to determine if it's executing on a virtual machine. If that analysis comes back negative, the trojan creates a registry entry to ensure that it runs every time the computer boots up. It then reaches out to its command-and-control (C&C) servers for instructions before it begins attempting to steal victims' financial information. Talos identified that one of the C&C domains was available, so it purchased it to monitor the scope of the campaign. In total, researchers logged 11,925,626 beacons from 3,165 unique IP addresses. Most of the systems that contacted the domain were located in Ukraine and the United States.
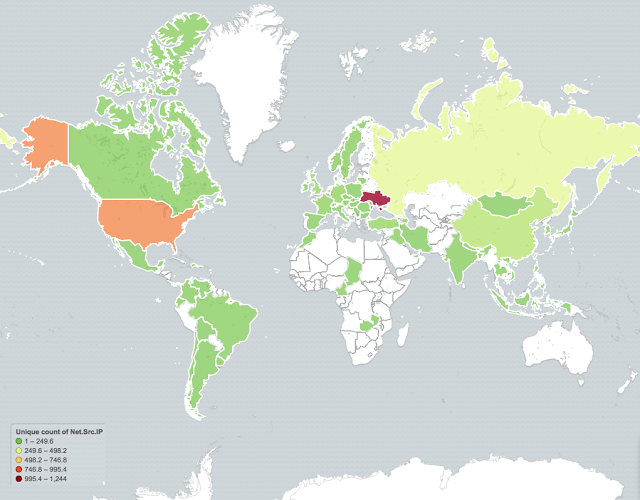
Affected Regions (Source: Cisco's Talos) Talos says this attack represents just one instance in an ongoing trend among bad actors:
As we saw repeatedly throughout 2017, attackers are increasingly attempting to abuse the trust relationship between organizations and their trusted software manufacturers as a means of obtaining a foothold within the environments they are targeting. As organizations deploy more effective security controls to protect their network environments attackers are continuing to refine their methodologies.
To learn how Tripwire can help your organization use foundational controls to defend against digital attackers, click here.

