
“Cybersecurity is the leading corporate governance challenge today, yet 87% of C-suite professionals and board members lack confidence in their company’s cybersecurity capabilities. Many CISOs and CSOs focus on implementing standards and frameworks, but what good is compliance if it does not improve your overall cybersecurity resilience?” – The CMMI Institute
Many organizations have Information Security Programs (ISPs), but many executives and boards do not know how to measure progress within these programs. They are therefore hesitant to believe any investment in technology will mitigate perceived or even unknown risks. Some organizations use regulated compliance standards such as PCI DSS or AICPA attestations as measures of their ISP. However, these standards do not fully cover the enterprise risk environment because they only focus on specific areas of risk or generic tenets of security. Due to the inability to measure cybersecurity and show reportable results, management is hesitant to fund something they cannot quantify. Therefore, information security leaders find it difficult to acquire funding to cover critical gaps in risk mitigation. Using compliance is the only available solution–however inadequate.
Introducing CMMI
Though CMMI is not an exact science, it is a way to present a quantifiable level of risk within the different elements of the ISP. CMMI can be a tool to provide the justification for necessary investment in information security. Many organizations confuse information security with information technology. New solution requests are viewed as enhancements or wish list items. For example, requests for additional full-time employees are looked upon as operating expense costs instead of enhancing the ISP. The difference is that risk is related to those requests and ultimately are reflected in the CMMI. There is a direct correlation between people, process and technology with the CMMI.
The History of CMMI
Information Systems Audit and Control Association (ISACA) created CMMI to measure business maturity and performance in a format that could be presented to executive management. But in recent years, highly visible breaches and the impacts of those breaches motivated boards to begin understanding the maturity of the organization’s ISP. CMMI answers this need. It is “a proven set of global best practices that drives business performance through building and benchmarking key capabilities,” per the CMMI Institute (a subsidiary of ISACA). It was originally created for the U.S. Department of Defense to assess the quality and capability of their software contractors. CMMI models can now help any industry build, improve and measure capabilities and performance.
Characteristics of the CMMI Model
There are five levels of maturity in the CMMI.
- Level 1 “Initial” is the organization with the least mature ISP. It is reactive, meaning it has poorly written procedures and unpredictable processes that have uncertain outcomes. Organizations at Level 1 may have limited information security expertise, with limited knowledge of strategy or tactics in dealing with threats.
- Level 2 “Managed” still maintains a reactive posture, but organizations at this level are more organized in information security related projects. Perhaps processes remain undocumented. The profile remains reactive.
- Level 3 “Defined” is a major leap from Level 2 in that the organization’s ISP becomes proactive in its approach to security incidents. Projects tailor their processes to clearly defined standards that are in line with business objectives.
- Level 4 “Quantitatively Managed” means that the organization has reached a level of maturity where processes, projects, and measurability are clearly defined and controlled. This environment requires an experienced information security team with strong leadership, budget, and support from executive management.
- Level 5 “Optimizing” is essentially building on what currently exists as a mature, quantitative, and qualitative ISP. Unfortunately, there are few organizations that can reach this level of maturity due to lack of expertise, limited talent pools, restrictive budgets, and lack of management support. All of this impedes the progress to maturity. ISPs become stagnant, technology becomes ineffective, and risk increases over time.
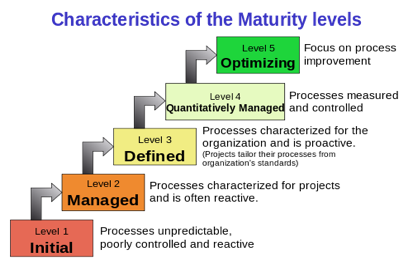
Characteristics of Maturity Levels
Focus Areas
Standards such as COBIT and ISO27001 have their individual CMMI models. In the past, these models did not cover all the areas needed in a CMMI model, so two elements of these were combined.
| Management of IT Security |
| Information Security Plan |
| Identity Management |
| User Account Management |
| Security Testing and Monitoring |
| Security Incident Definition |
| Protection of Security Technology |
| Cryptographic Key Management |
| Malicious Software Prevention |
| Network Security |
| Exchange of Sensitive Data |
| Compliance |
The table above includes the areas used in a CMMI model, which was recently presented to an executive leadership team. It was so well received, the CEO presented it to the board. This experience provided proof that executives are more likely to financially buy in when there are metrics showing the progress of their organization’s ISP.
Looking Ahead
ISPs are required for any business handling customer or sensitive data. In some industries, compliance programs measure the ISP, but only to specific standards. A CMMI model based on global industry standards for cybersecurity provides insight to and gauges the level of maturity of the ISP as it pertains to the enterprise. CMMI models are gaining in popularity. They help information security teams educate executive leadership teams on how well the ISP is supported and maintained. Additionally, they can continue to provide effective protection against inside and external threats. In summary, the CMMI model provides a bridge towards an organization’s understanding of the information security team responsible for identifying, relaying and projecting future risks as well as formulating a comprehensive and validated justification when requesting funds for future solutions.

About the Author: With nearly 24 years in Information Security, Nigel Sampson has gained a great depth of knowledge and experience in the Information Security realm. His roles have ranged from Network Manager and IT Director, to VP of Risk Management and Information Security Officer. Covering diverse industries such as Healthcare, Banking, Government, and Entertainment. Nigel honed his leadership skills across different organisations and has managed teams of different sizes maintaining a pace-setting but democratic management style. Over the last 10 years he built several Information Security Programs from the ground up, including deploying 6 global information security solutions for a global leader in process optimisation and assisting a federally funded transport agency reach its first Tier 1 PCI certification. He is a dedicated and passionate Information Security leader that utilises his technical and consulting skills to bind Information Security Programs to business objectives. Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
Mastering Security Configuration Management
Master Security Configuration Management with Tripwire's guide on best practices. This resource explores SCM's role in modern cybersecurity, reducing the attack surface, and achieving compliance with regulations. Gain practical insights for using SCM effectively in various environments.

