
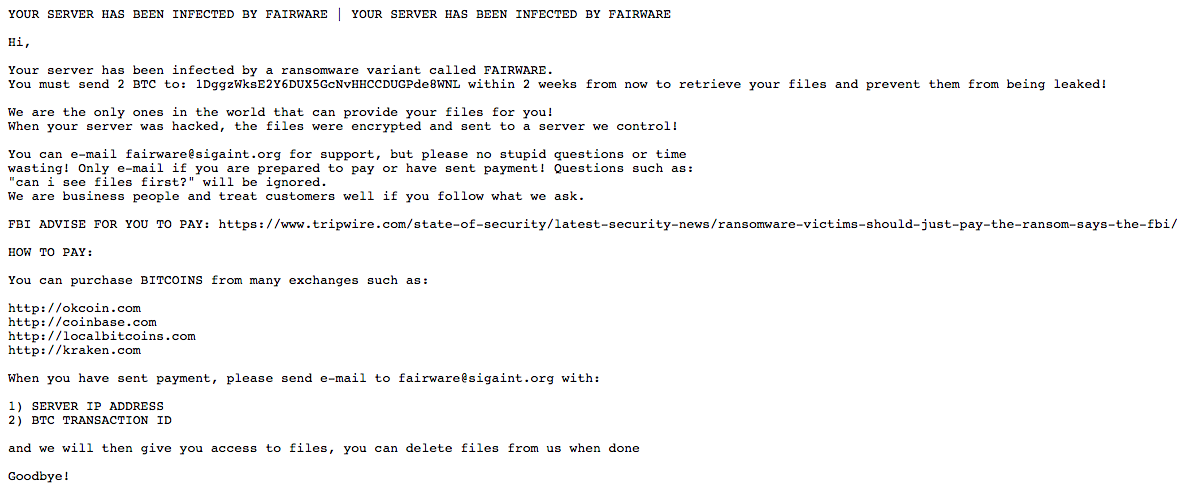
Linux users are reporting a new ransomware called "FairWare" played a part in taking down their websites. News of the ransomware first surfaced in a post on Bleeping Computer's forums. According to the victim, attackers likely brute-forced or intercepted the password for their Linux machine. Once they acquired access, the baddies logged into the Linux servers for the website, deleted the web folder, and left a Pastebin message demanding a ransom payment of two Bitcoins for the return of the files. If the victim doesn't pay the ransom in two weeks, the attackers warned they won't return the files and will instead leak them to an unknown location. They're not looking for the victim to ask questions, either. As evidenced by their ransom note, they know they're in control:
"We are the only ones in the world that can provide your files for you! When your server was hacked, the files were encrypted and sent to a server we control! "You can e-mail [email protected] for support, but please no stupid questions or time wasting! Only e-mail if you are prepared to pay or have sent payment! Questions such as: 'can i see files first?' will be ignored. We are business people and treat customers well if you follow what we ask."
On a personal note, the attackers then link to an article I wrote on the FBI's recommendations that some ransomware victims just pay the ransom.
The malware developers clearly want to get paid. But doing so doesn't guarantee victims the return of their files, as Bleeping Computer security expert Lawrence Abrams rightly points out:
"At this time it is unknown of the attacker actually retains the victim's files and will return them after ransom payment. Though all ransomware victims should avoid paying a ransom, if you do plan on paying, it is suggested you verify they have your files first."
FairWare's authors are asking that victims direct their payments to 1DggzWksE2Y6DUX5GcNvHHCCDUGPde8WNL. At this time, no one has submitted payment to that Bitcoin wallet. This isn't the first ransomware to target Linux users. In November 2015, news surfaced of Linux.Encoder.1 targeting Linux machines, encrypting users' files, and demanding one Bitcoin in exchange for the decryption key. Fortunately, it took researchers less than two weeks to develop a free decryption tool for the ransomware. Those behind FairWare want users to pay the ransom. But this should be the last resort for victims, as doing so legitimizes ransomware as a form of business. Users should instead prepare themselves for a ransomware infection by backing up their files, avoiding suspicious links and email attachments, and keeping their systems up to date. For more ransomware prevention tips, please click here. You can also learn more about ransomware in general here.

