It’s no surprise that industrial environments have become increasingly valuable targets for malicious behavior. The State of Security has featured many cybersecurity events across myriad industrial verticals, including but not limited to chemical manufacturing, transportation, power generation and petrochemical. Several of these industries have taken great strides in improving their defense posture, but this was primarily driven as a result of governmental regulatory compliance requirements.
Most organizations with Industrial Control Systems (ICS) fall into one of two categories: regulated and non-regulated. For those subject to governmentally imposed regulatory requirements, the selection of a cybersecurity framework is obviously compelling.
Even if your organization is not subject to any regulatory requirements, the following section should still be of interest, especially if your industry is moving in this direction in the near future, or you’d like to better understand how regulated industries have been measuring the state of their security posture.
Regulated Approach
Efforts of the North American Electric Reliability Corporation Critical Infrastructure Protection (NERC CIP), and the Nuclear Energy Institute (NEI) 08-09 requirements have had a positive effect on the industry. These specialized requirements have been tailored to for the electric utility and nuclear power generation sectors, respectively. While these, as well as other lesser known requirements can be burdensome, they are intended to improve the visibility, implement protective controls, and establish continuous monitoring.
But what about those environments that are not subject to these regularity requirements?
Consider extending the reach of your internal compliance programs and technology into assets and environments that didn’t meet the thresholds of being subject to regulatory compliance. The time and effort that your organization has put into deploying controls for security and compliance can more often than not be re-deployed and extended into additional areas of the business and industrial process quickly, cost effectively, and more easily than the initial deployment. This will still provide meaningful benefits without being subject to audits or Reliability Standard Audit Worksheets (RSAWs).
Another approach that regulated utilities should consider is to map another cybersecurity framework into the environment. This will offer a different perspective on some of the very same controls that are in place, and will also reveal gaps in coverage that are used in alternate frameworks.
Tripwire Enterprise makes what would initially appear as a daunting task quite easy. Tripwire Enterprise policies can be deployed “side-by-side” within your environment without having to re-check devices with new rules.
General Approach
For most industrial verticals, there is no mandatory framework of hardening guidelines that have been built and refined for each use case. So, where do you start?
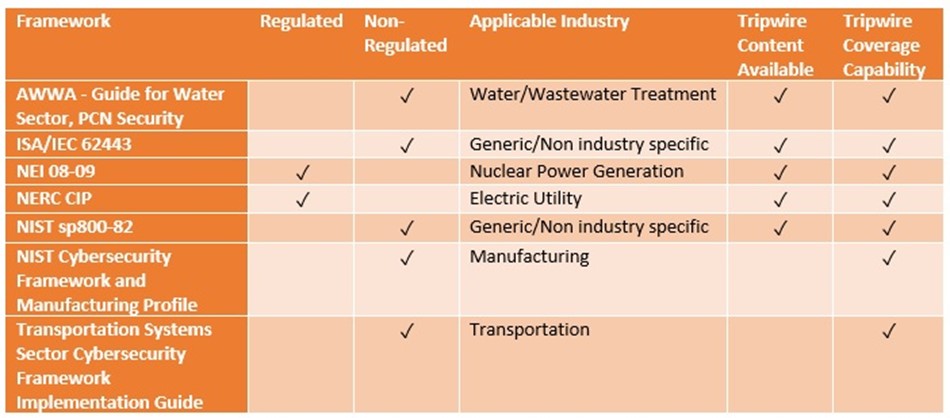
First, make sure that a framework for your industry doesn’t already exist. Some common frameworks include:
- American Water Works Association (AWWA) – Guide for Water Sector
- Transportation Systems Sector Cybersecurity Framework Implementation Guide
- NIST Cybersecurity Framework and Manufacturing Profile (NIST IR8183)
If your search came up short, there are some fantastic generic industrial cybersecurity frameworks available. At this stage of your cybersecurity lifecycle, don’t be overwhelmed with trying to decide which standard to adopt or follow. The most important decision is to adopt one. Doing nothing can have major consequences, and just getting started is sometimes the hardest part.
Here’s a chart to help you navigate some of the available frameworks:
Applying the controls suggested by each of these respective frameworks can be an overwhelming task if you’re starting from nothing, but don’t let that discourage you. Tripwire has some fantastic tools in its portfolio that can assist with the implementation.
Take a look at Tripwire’s ICS Security Suite as a great starting point. Whether the journey to secure your Industrial Control System has just begun or you’re a seasoned professional, choosing the correct Industrial Cybersecurity Framework can be a daunting task. Although you may not fit directly within a particular scenario, there are plenty of sources to provide insight about some of the more prominent frameworks available today.
Zero Trust and the Seven Tenets
Understand the principles of Zero Trust in cybersecurity with Tripwire's detailed guide. Ideal for both newcomers and seasoned professionals, this resource provides a practical pathway to implementing Zero Trust, enhancing your organization's security posture in the ever-evolving digital landscape.

