
Part of Ukraine's capital, Kiev, lost power on December 17-18, 2016, due to a digital attack. The operation, which occurred nearly one year after BlackEnergy targeted western Ukrainian power company Prykarpattyaoblenergo with KillDisk malware, pushed networks and Supervisory Control and Data Acquisition (SCADA) systems at utility Ukrenergo "outside normal parameters." Security researchers believe bad actors hid in the company's network for six months, all the while conducting reconnaissance of their target, before springing into action. An attack that shuts off critical energy systems doesn't happen every day. Similarly, researchers don't frequently discover malware with such destructive potential, but it does happen. Case in point, researchers have discovered malware that could have caused the outage on Kiev's power grid. It has capabilities that allow it to not only cause "significant harm" to electric power systems but to also damage other critical infrastructure.
Inside the Modular Industroyer
The modular malware, detected by Slovakian security company ESET as "Win32/Industroyer," disrupts the processes of industrial control systems (ICS). It works by installing a main backdoor component that controls other components. These modules include four payload elements that gain direct control of switches and circuit breakers at a substation by targeting communication protocols defined in four International Electrotechnical Commission (IEC) standards. ESET elaborates on this point further:
"Industroyer's dangerousness lies in the fact that it uses protocols in the way they were designed to be used. The problem is that these protocols were designed decades ago, and back then industrial systems were meant to be isolated from the outside world. Thus, their communication protocols were not designed with security in mind. That means that the attackers didn’t need to be looking for protocol vulnerabilities; all they needed was to teach the malware 'to speak' those protocols."
The protocols abused by Industroyer's four modules are as follows: IEC 60870-5-101, IEC 60870-5-104, IEC 61850 and OLE for Process Control Data Access (OPC DA).
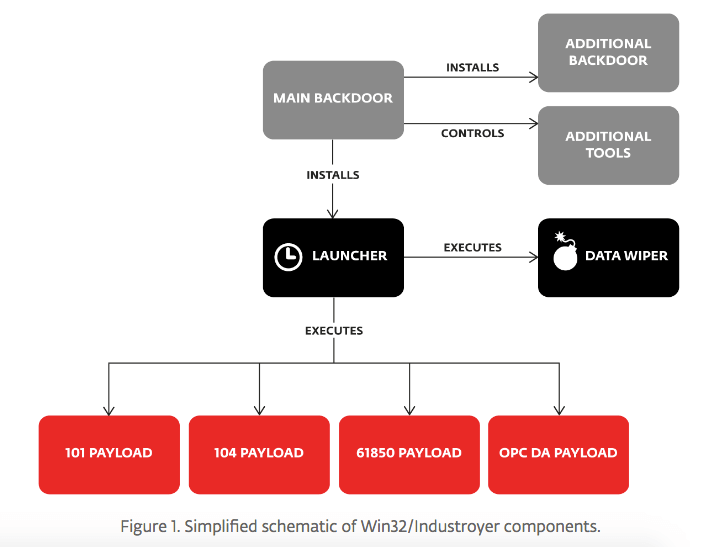
An Industroyer infection begins when the malware installs its main backdoor. This core component connects via HTTPS to one of several command-and-control (C&C) servers, most of which are running Tor software. Every sample of the threat detected by ESET contained the same hardcoded proxy address on the local network, meaning the attackers configured the malware to target a single organization. To optimize the success of an infection, Industroyer's handlers had the option of defining the malware's hours of operation. For instance, they could prevent it from executing until after normal business hours to help the threat evade detection. The main backdoor is essential to retrieving a launcher component from the C&C that loads four payload components and a data wiper utility. Without network access, the malware can't make the necessary exchange to obtain this tool. It's up to the main backdoor to facilitate this communication. In the event someone detects or disables the main backdoor, Industroyer comes equipped with an alternate backdoor. This secondary access program is a trojanized version of the Windows Notepad app. On launch, the app executes malicious code that connects to a C&C that's different than the main backdoor's server. A successful response yields shellcode that the malware loads directly into memory and executes. From there, the launcher begins immediately installing four payload components:
- 101 Payload Component: A DLL that abuses IEC 101, an international standard used for monitoring and controlling electric power systems and Remote Terminal Units (RTU). It uses a configuration file to attempt to end legitimate communication and initiate malicious contact with a device over serial connection using RTU. It then switches the state of Information Object Addresses (IOAs) from Off to On to Off again.
- 104 Payload Component: A file named for IEC 104, which extends IEC 101 so that the protocol can transmit over TCP/IP. It terminates the process responsible for legitimate IEC 104 communication, reads a configuration file, and uses it to find IP addresses through which it can interact with IOAs with a single command. After confirming the IOAs that belong to a single command type, the component places those into an infinite loop that flips their states between On and Off at every loop step.
- 61850 Payload Component: A standalone malicious tool named after IEC 61850, a standard for a protocol which enables multi-vendor communication between devices that monitor and protect electrical substation automation systems. It retrieves a list of devices capable of communication via IEC 61850 from the launcher component, at which point it begins targeting them with MMS getNameList requests. The payload then enumerates objects, uses more MMS requests to enumerate variables, and looks in the responses for "CSW," a string which represents the logical nodes used to control circuit breakers and switches.
- OPC DA Payload Component: A tool that opens a client for OLE for Process Control (OPC) Data Access, which allows for real-time data exchange between distributed components. The component enumerates all OPC servers on execution and then enumerates all OPC items. It attempts to change the state of any OPC item it finds.
An hour or two after downloading its DLLs, Industroyer's launcher component installs the data wiper component. Known as haslo.dat, this tool first enumerates all keys in the registry that list Windows services and tries to set the registry value ImagePath with an empty string, thereby making the operating system unbootable. It then gears up for its main event. As explained by ESET in their report (PDF) on Industroyer:
"The next step is actual deletion of file contents. The component enumerates files with specific file extensions on all drives connected to computer, from C:\ to Z:\. It should be noted that during enumeration the component skips files that are located in subdirectory that contains Windows in its name. "The component rewrites file content with meaningless data obtained from newly allocated memory. In order to perform this operation thoroughly the component attempts to rewrite files twice. The first attempt happens once the file is found on a drive. If the first attempt is unsuccessful then the wiper malware makes a second attempt, but before that the malware terminates all processes except those included in a list of critical system processes."
Industroyer's data wiper targets files that show up in a standard environment, like Windows binaries, Microsoft SQL server files and files specific to ICS environments. It rewrites a portion of each of these files and attempts to terminate all processes except its own. Successful termination causes the system to crash and become unresponsive.
A 'Sophisticated Piece of Malware'
ESET's researchers have not confirmed at this time whether Industroyer was responsible for Ukraine's power outage in December 2016. But given its modular design, which includes extra elements like a custom-made port scanner tool and a denial-of-service (DoS) utility, the malware is a likely candidate. The threat research team at ESET agrees:
"We can definitely say that the Win32/Industroyer malware family is an advanced and sophisticated piece of malware that is used against industrial control systems. However, it should be noted that the malware itself is just a tool in the hands of an even more advanced and very capable malicious actor. Using logs produced by the toolset and highly configurable payloads, the attackers could adapt the malware to any comparable environment."
To protect against sophisticated threats like Industroyer, organizations need to invest in a solution that monitors their ICS endpoints for anomalous behavior. At the same time, industry and government actors need to discuss how to better secure ICS communication protocols such as those defined in the standards abused by Industroyer. It's an important conversation given the digital security risks confronting electric power systems and other critical infrastructure today. For more thoughts concerning ICS security, please download this resource here.
Achieving Resilience with NERC CIP
Explore the critical role of cybersecurity in protecting national Bulk Electric Systems. Tripwire's NERC CIP Solution Suite offers advanced tools for continuous monitoring and automation solutions, ensuring compliance with evolving standards and enhancing overall security resilience.

