
KillDisk malware has moved away from wiping infected computers of their stored data and has evolved into ransomware. Researchers at ICS/SCADA security firm CyberX recently came across a new KillDisk variant. After reverse-engineering it, they found that the malware displayed a pop-up ransom message demanding victims pay 222 Bitcoins in exchange for the decryption key. That's 206,000 USD--more than most other ransomware demands.
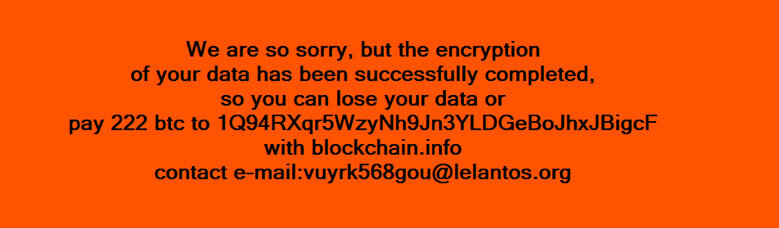
KillDisk ransom note. (Source: CyberX) Phil Neray, VP of marketing at the Massachusetts-based company, provides more details about KillDisk's updated form:
"The new malware encrypts both local hard-drives and any network-mapped folders that are shared across the organization, using a combination of RSA 1028 public key and AES shared key algorithms, where each encrypted file has its own AES key. The contact email uses a secure, anonymous email service (lelantos) to hide the identity of the attackers. We believe the malware is being distributed via malicious Office attachments."
CyberX thinks a group known as TeleBots revamped the wiper malware into ransomware. It's the same threat actor that launched malware attacks against the Ukrainian financial sector in the second half of 2016 using KillDisk. TeleBots is also an evolution of Sandworm, a Russian espionage gang which exploited CVE-2014-4114 to attack NATO and other Western organizations in 2014 and used KillDisk against several Ukrainian power companies in December 2015. TeleBots has much to gain from updating its malware. As noted by Catalin Cimpanu of Bleeping Computer, KillDisk's ransomware component makes it easier for the gang to hide its tricks. It also means the group can extort industrial organizations, targets which can't afford to not access their data or shut down their networks to scrub them of malware. Acknowledging the threat posed by TeleBots, industrial organizations need to take certain steps to protect themselves. They should first and foremost invest in security awareness training for all employees and segment operation technology (OT) networks as much as possible. They should also consider investing in a solution that can monitor industrial control systems for anomalous behavior.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

