
In May 2017, an updated version of WannaCry ransomware struck a minimum of 200,000 organizations in over 150 countries. It did so by abusing a Windows SMB vulnerability (MS17-010) using exploit code developed by the NSA and leaked online by The Shadow Brokers. As we all know, however, not all attack campaigns automatically exploit vulnerable software. Proofpoint's The Human Factor Report 2017 reveals that a higher percentage of actors incorporated social engineering techniques into their attacks in 2016 than in the previous year. Let's examine Proofpoint's findings and what they mean for organizations looking to protect their users against social attacks.
Human-Driven Exploits in the Driver's Seat
Vulnerability drive-by attacks took a backseat to social attacks in 2016. According to Proofpoint's report, human-centric or "click-enabled" attacks accounted for 99 percent of email-based financial fraud techniques by the end of the year. Similarly, nine in 10 malicious URL messages pointed to credential phishing sites rather than landing pages for exploit kits like RIG and Bizarro Sundown.
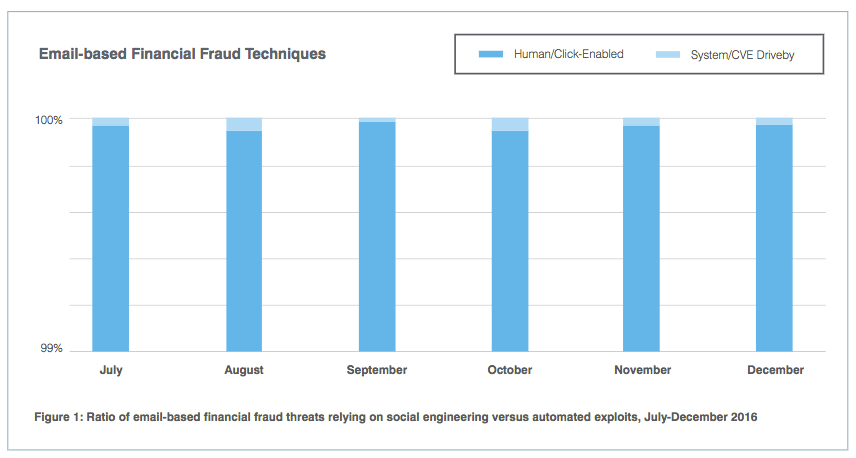
The Human Factor Report 2017 page 8. (Source: Proofpoint)
Threat on Arrival: When to Expect Which Email-Based Threats
E-mail-based "click-enabled" threats arrived on each day of the week, but some came in larger droves than others depending on the day. For instance, the combined total of attachment messages and URL messages delivered on Sundays amounted to less than 25,000 instances. Sunday was the only day on which URL messages numbered more than attachment messages. All other days, malicious link-based missives remained below 50,000 instances, peaking on Tuesdays and Thursdays. Meanwhile, attachment messages consistently remained above 150,000 instances on most other days, with their peak of over 300,000 attacks arriving on Thursdays. Proofpoint found that the bulk of each day's attachment messages consisted of ransomware. As its researchers explain in their report:
"On Thursday, Ransomware message volumes were much higher on Thursday than the other days of the week, driven primarily by high-volume campaigns that sent the Locky strain. With few exceptions, ransomware was the only category of malware sent on weekends."
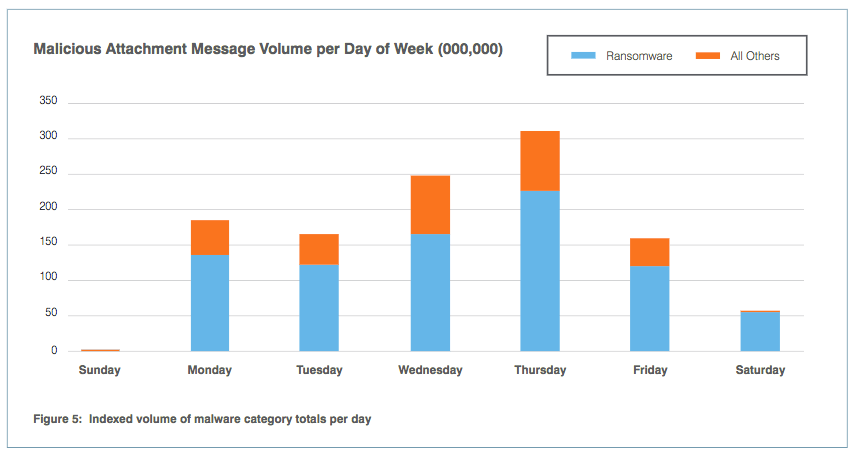
The Human Factor Report 2017 page 10. (Source: Proofpoint) Even so, other threats contributed to the daily number of attachment messages. Banking trojans, credential stealers and downloaders all played a part, but their combined total never accounted for much more than a third of malicious attachment messages. In general, keyloggers and backdoors arrived early in the week, allowing attackers to steal credentials all week. By contrast, POS campaigns arrived later in the week to capitalize on the smaller number of employees working the weekends.
Credential Phishing Lures and Click Rates
The most prolific phishing lures of 2016 leveraged well-known technology brands to generate clicks. Apple accounts came in on top by accounting for a quarter of all phishing lures, followed by Microsoft Outlook Web Access (OWA) and Google Drive at 17.0 percent and 12.9 percent, respectively. Delivery volume did not line up exactly with click rates in large-scale (20,000+ messages) email fraud campaigns, however. Lures that used Dropbox and Adobe generated click rates greater than 10 percent. Google Drive-based lures registered a 5.1 percent click rate, whereas Microsoft OWA and Apple clocked in only at 2.8 percent and 1.2 percent, respectively. By contrast, local post office service lures saw a click rate of 78.6 percent in small campaigns (100+ messages). Broken down even further, nearly half of all clicks (44.7 percent) occurred on Windows machines. Sixty-six percent of those Windows-based clicks occurred on operating systems outside of "mainstream support" like Windows 7, whereas nearly a fifth (19 percent) of clicks on Windows PCs took place on unsupported OS platforms like Windows XP, Windows Vista and Windows 2000. The second largest OS of user clicks was Android at 37 percent, followed by Mac OS X (8.3 percent), iOS (5.2 percent), and Other (4.8 percent). Not surprisingly, user clicks picked up at the beginning of the work day, peaked 4-5 hours later, and slowly dropped off into the evening. Figure 11 reveals this trend.
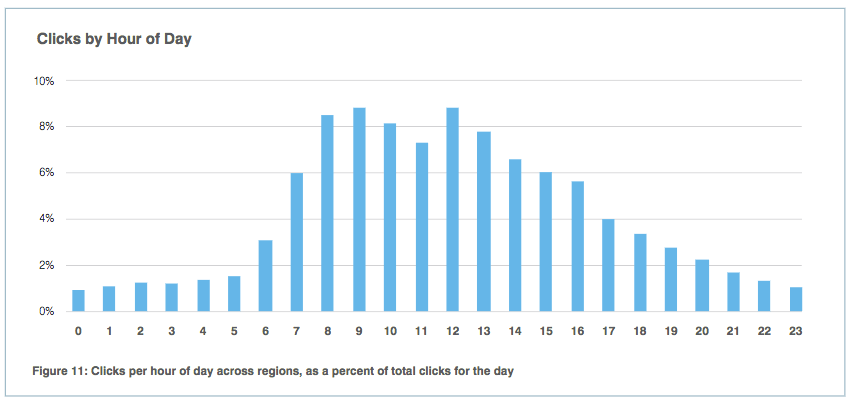
The Human Factor Report 2017 page 14. (Source: Proofpoint) But Figure 11 depicts another striking finding. Proofpoint elaborates:
"The most striking takeaway from Figure 11 is that users click on malicious URLs at every hour of the day. Whether at work or at home, day or night, users are clicking on URLs that can lead to phishing pages and malware downloads."
On business days, it took most users less than an hour to click on a malicious URL after delivery. More than a quarter (25.5 percent) of clicks occurred within 10 minutes of delivery. Meanwhile, 98.3 percent of clicks occurred in a week.
Recommendations
Every organization needs to focus on email as an attack vector. They can do so by using behavior analysis and other threat detection services to scan email attachments and URLs for malicious code and behavior. They should also conduct security awareness training with their employees, implement foundational security controls on mobile devices with access to the corporate network, and strengthen their incident response capabilities. For more findings regarding click-based attacks in 2016, download Proofpoint's report here.

